Posted on: July 26th, 2013
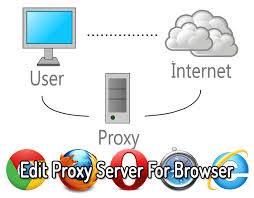
What a proxy server is? Let’s find out:
The article will explain what actually proxy server is and how it works? There are certain things that one needs to understand and all the pertinent terms are stated below.
Http Headers:
Internet itself is a huge world and people from all over the world are somehow connected to it. What we all need to understand is that what actually happens when you go to a website. For example we visit yahoo.com. Following are the things that happen.
Read the rest of this entry »
Posted on: July 24th, 2013
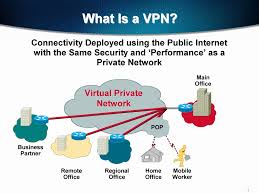 A VPN or virtual private network utilizes public access of the internet via remote access, LAN to LAN internet (Local Area Network) and controlled access. This allows the employees of a company to access their company’s corporate intranet no matter where they are located. While the VPN uses public access to connect people to the intranet of their specific company, the security features keep those who are not allowed into the intranet from connecting.
A VPN or virtual private network utilizes public access of the internet via remote access, LAN to LAN internet (Local Area Network) and controlled access. This allows the employees of a company to access their company’s corporate intranet no matter where they are located. While the VPN uses public access to connect people to the intranet of their specific company, the security features keep those who are not allowed into the intranet from connecting.
Along with the convenience factor of the VPN come the natural problems with using them. There are truly some advantages and disadvantages to using the VPN, some of the disadvantages include the potential of running into incompatible vendor software packages. Some incompatibility is to be expected when there are choices of access to the network from Windows, Mac iOS, and tablet devices. Whether the disadvantages outweigh the advantages depends on the company, the individuals using the intranet and a number of other factors. Read the rest of this entry »

Posted on: July 22nd, 2013
 Search engine optimization helps your site improve its visibility on the internet. For those of you who have recently become aware of SEO, part artform and statistics with part voodoo and witchcraft, it is a little scary to start the process. Luckily there are tools available to help you choose the key words and get them implanted on your website. Most are free to use, some have subscriptions to help you in more complicated matters related to SEO.
Search engine optimization helps your site improve its visibility on the internet. For those of you who have recently become aware of SEO, part artform and statistics with part voodoo and witchcraft, it is a little scary to start the process. Luckily there are tools available to help you choose the key words and get them implanted on your website. Most are free to use, some have subscriptions to help you in more complicated matters related to SEO.
SEOmoz is a site that includes the ‘Beginners Guide to SEO’ as a tutorial to teach you how search engines work. A quick read of this tutorial will give the beginner enough knowledge regarding keyword research and more that becomes necessary in making sure your site’s rankings improve. The basic service that includes the tutorial and instructions are free, or for a subscription rate of under $100/month you can join SEOmoz PRO and download the guide for future use. Read the rest of this entry »
Posted on: July 20th, 2013
 When someone types in a search term into a search engine, that search engine’s job is to find the occasions that that term is used online, run an analysis of that includes counting the number of times a particular page with that term is referred to on other sites and return the resulting list of potential websites for the user to click on. Somewhere in the massive list of potentially correct websites for the user to click on.
When someone types in a search term into a search engine, that search engine’s job is to find the occasions that that term is used online, run an analysis of that includes counting the number of times a particular page with that term is referred to on other sites and return the resulting list of potential websites for the user to click on. Somewhere in the massive list of potentially correct websites for the user to click on.
Although there is a way to purchase your site’s way to the top, that has nothing to do with actual search engine optimization and more to do with the budget your company has for marketing. The Off-Page SEO is work that is done as named, off of the page of the internet. There are two ways to optimize your site to make it easier for search engines to find and to increase the chances that your site will be listed among the top ten or twenty options. Then there is the On-Page SEO work that takes place on the page itself. Read the rest of this entry »
Posted on: July 18th, 2013
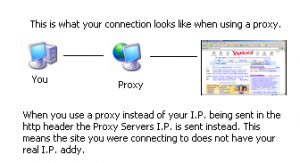 When you access the internet your computer does so leaving clear traces of your identity through the unique IP address your computer has. These IP addresses can be used in masse by companies and corporations to ban the use of certain websites from being accessed through their IP addresses. Schools prevent access to some social media sites, porn sites and others. Through the use of a proxy server, the user can access those sites without leaving a trace of their own IP address and can bypass the restrictions at work or school that prevents them from accessing certain websites.
When you access the internet your computer does so leaving clear traces of your identity through the unique IP address your computer has. These IP addresses can be used in masse by companies and corporations to ban the use of certain websites from being accessed through their IP addresses. Schools prevent access to some social media sites, porn sites and others. Through the use of a proxy server, the user can access those sites without leaving a trace of their own IP address and can bypass the restrictions at work or school that prevents them from accessing certain websites.
There are a number of reasons why you may not want your IP address linked to certain websites. Read the rest of this entry »
Posted on: July 16th, 2013
 With the issue of identity theft becoming more and more a public problem internet security has become an issue for anyone with internet access. While Apple brags about their security measures, yes, they have been hacked several times, most internet access is done through Microsoft’s Internet Explorer. As a result of a larger percentage of people using IE to access the internet, the IE security settings have become tougher with each new version that has been released. Malicious ActiveX or Java based viruses or malware infested sites can infect a users’ computer and cause serious problems for the user. IE allows users to classify the sites they visit and configure their Explorer settings for websites that are in different ‘zones’.
With the issue of identity theft becoming more and more a public problem internet security has become an issue for anyone with internet access. While Apple brags about their security measures, yes, they have been hacked several times, most internet access is done through Microsoft’s Internet Explorer. As a result of a larger percentage of people using IE to access the internet, the IE security settings have become tougher with each new version that has been released. Malicious ActiveX or Java based viruses or malware infested sites can infect a users’ computer and cause serious problems for the user. IE allows users to classify the sites they visit and configure their Explorer settings for websites that are in different ‘zones’.
For the uninitiated, there are four different ‘zones’ that IE classifies site pages. These include: Trusted, Restricted, Internet/Intranet and Local. Read the rest of this entry »
Posted on: July 2nd, 2013
 One of the most important aspects of modern life is our privacy. One of the biggest problems in terms of privacy is the problem of protecting the privacy online. Any attempt to protect one’s privacy online begins with policies. These policies are extremely complex and invariably confusing. Their language also seems alien since most of these policies are designed to hold up in the complex legal systems.
One of the most important aspects of modern life is our privacy. One of the biggest problems in terms of privacy is the problem of protecting the privacy online. Any attempt to protect one’s privacy online begins with policies. These policies are extremely complex and invariably confusing. Their language also seems alien since most of these policies are designed to hold up in the complex legal systems.
Luckily, a few individuals from the University of Victoria, Canada created the CATSMI Project (The Canadian Access to Social Media Information Project). This project analyses the policies of the top 20 social media websites and provides a plain worded description on what to expect from the policies with respect to – Read the rest of this entry »
Posted on: June 24th, 2013

Data Point
One of the first aspects to be considered is the importance of the Data Point. For product developers, it holds immense importance since it allows them to understand the main issues. Similarly, from the point of view of the system admins, it’s a great option to get a prior warning of a new threat and ensure that the system is well prepared for an onslaught.
Data Sources
There is no surprise in the fact that most IT companies are putting in tremendous amounts of efforts to gather all kinds of data.Most products nowadays include a feature known as the phone home which reports back to the base station as soon as a thread is spotted. Read the rest of this entry »
Posted on: June 22nd, 2013
 Modern technology has made it extremely difficult to do basic activities such as walking on the roads or driving a car without texting or fidgeting with mobile phones and androids. However, the Android allows users to text or email and walk or drive without even bothering to look at the screens. How? Simply ask and we will let you know.
Modern technology has made it extremely difficult to do basic activities such as walking on the roads or driving a car without texting or fidgeting with mobile phones and androids. However, the Android allows users to text or email and walk or drive without even bothering to look at the screens. How? Simply ask and we will let you know.
- How to Email without looking at the Android screens
- The first step is to press the mic icon and then saying “Send Email”.
- The next step involves identifying the person you want to send the mail to by saying “To (contact name)”
- Then one needs to state the subject by saying “Subject (content of the subject)”
- Finally, in order to compose the body of the Email, users need to say “Message (body of the message along with speaking out the punctuation marks)”.
How to SMS without looking at the Android screens
- The processes of sending the SMS as well as sending an E-mail are quite similar. You simply need to say “Send Text To” and then the “contact name and the content”. Read the rest of this entry »

Posted on: June 2nd, 2013
 The task of protecting the data was never an easy one. However, with the advent of internet viruses and hackers who are regularly developing new techniques to exploit or steal an individual’s data, the task has become a lot more difficult. There are cases where such attacks may not be as harmful to individual users. However, they can be a nightmare for financial institutions and the popular websites. The most common method to initiate a MITM attack is by uploading malware onto the user’s machine. However, the accuracy of this method is debatable as the method does not work sometimes.
The task of protecting the data was never an easy one. However, with the advent of internet viruses and hackers who are regularly developing new techniques to exploit or steal an individual’s data, the task has become a lot more difficult. There are cases where such attacks may not be as harmful to individual users. However, they can be a nightmare for financial institutions and the popular websites. The most common method to initiate a MITM attack is by uploading malware onto the user’s machine. However, the accuracy of this method is debatable as the method does not work sometimes.
What is the MITM attack
The Man in the Middle (MITM) attack is also known as the Bucket Brigade attack and the Janus attack. The hacker place themselves in between two parties and make them believe that it is a private conversation in between the two whereas the conversation is actually controlled by the hacker. However, a Man in the Middle (MITM) attack can only be successful when the hacker is successful in forming a mutual authentication in between both parties. This is where the SSL (Secure Sockets Layer) protocols become so important as they are used to authenticate the parties by using a mutually trusted authority for certification.
How does the MITM attack work
In the typical MITM attack, the hackers use a WiFi router to intercept user communications. The hacker uses a few malicious programs to assist him/ her to intercept the user communications which take place on the router. The basic process is that the hackers configure their laptops as a Wifi hotspot by choosing common names which are commonly used in public areas such as a coffee shop or a restaurant. Once a user reaches out to eCommerce sites using this WiFi, the hacker saves this information for later use. For example, two people want to converse while a third (hacker) wants to eavesdrop and have a false conversation with one of the two. It begins when the first person asks the other for the public key. If the second person provides this key to the first, the third person (hacker) uses this key to begin a conversation with the first person by providing the key which the second one gave. In this way, the first person easily believes that he/ she is actually having an authentic conversation while it is not at all true.
How to prevent MITM attacks
The best defence against a Man in the Middle attack is only on the router side as users can have no control over the security of their transactions. However, what they can have is an extremely strong level of encryption which goes a great way in enhancing the level of security for the referred transactions. In such cases, the clients request is only authenticated with the help of a digital certificate and only then is the connection established. Another method of prevention of these Man in the Middle attacks is by never connecting to open WiFi networks directly. By using plug ins such as ForceLTS and HTTPS Everywhere, the connection can be made much more secure.



 A VPN or virtual private network utilizes public access of the internet via remote access, LAN to LAN internet (Local Area Network) and controlled access. This allows the employees of a company to access their company’s corporate intranet no matter where they are located. While the VPN uses public access to connect people to the intranet of their specific company, the security features keep those who are not allowed into the intranet from connecting.
A VPN or virtual private network utilizes public access of the internet via remote access, LAN to LAN internet (Local Area Network) and controlled access. This allows the employees of a company to access their company’s corporate intranet no matter where they are located. While the VPN uses public access to connect people to the intranet of their specific company, the security features keep those who are not allowed into the intranet from connecting. Search engine optimization helps your site improve its visibility on the internet. For those of you who have recently become aware of SEO, part artform and statistics with part voodoo and witchcraft, it is a little scary to start the process. Luckily there are tools available to help you choose the key words and get them implanted on your website. Most are free to use, some have subscriptions to help you in more complicated matters related to SEO.
Search engine optimization helps your site improve its visibility on the internet. For those of you who have recently become aware of SEO, part artform and statistics with part voodoo and witchcraft, it is a little scary to start the process. Luckily there are tools available to help you choose the key words and get them implanted on your website. Most are free to use, some have subscriptions to help you in more complicated matters related to SEO. When someone types in a search term into a search engine, that search engine’s job is to find the occasions that that term is used online, run an analysis of that includes counting the number of times a particular page with that term is referred to on other sites and return the resulting list of potential websites for the user to click on. Somewhere in the massive list of potentially correct websites for the user to click on.
When someone types in a search term into a search engine, that search engine’s job is to find the occasions that that term is used online, run an analysis of that includes counting the number of times a particular page with that term is referred to on other sites and return the resulting list of potential websites for the user to click on. Somewhere in the massive list of potentially correct websites for the user to click on. When you access the internet your computer does so leaving clear traces of your identity through the unique IP address your computer has. These IP addresses can be used in masse by companies and corporations to ban the use of certain websites from being accessed through their IP addresses. Schools prevent access to some social media sites, porn sites and others. Through the use of a proxy server, the user can access those sites without leaving a trace of their own IP address and can bypass the restrictions at work or school that prevents them from accessing certain websites.
When you access the internet your computer does so leaving clear traces of your identity through the unique IP address your computer has. These IP addresses can be used in masse by companies and corporations to ban the use of certain websites from being accessed through their IP addresses. Schools prevent access to some social media sites, porn sites and others. Through the use of a proxy server, the user can access those sites without leaving a trace of their own IP address and can bypass the restrictions at work or school that prevents them from accessing certain websites. With the issue of identity theft becoming more and more a public problem internet security has become an issue for anyone with internet access. While Apple brags about their security measures, yes, they have been hacked several times, most internet access is done through Microsoft’s Internet Explorer. As a result of a larger percentage of people using IE to access the internet, the IE security settings have become tougher with each new version that has been released. Malicious ActiveX or Java based viruses or malware infested sites can infect a users’ computer and cause serious problems for the user. IE allows users to classify the sites they visit and configure their Explorer settings for websites that are in different ‘zones’.
With the issue of identity theft becoming more and more a public problem internet security has become an issue for anyone with internet access. While Apple brags about their security measures, yes, they have been hacked several times, most internet access is done through Microsoft’s Internet Explorer. As a result of a larger percentage of people using IE to access the internet, the IE security settings have become tougher with each new version that has been released. Malicious ActiveX or Java based viruses or malware infested sites can infect a users’ computer and cause serious problems for the user. IE allows users to classify the sites they visit and configure their Explorer settings for websites that are in different ‘zones’. One of the most important aspects of modern life is our privacy. One of the biggest problems in terms of privacy is the problem of protecting the privacy online. Any attempt to protect one’s privacy online begins with policies. These policies are extremely complex and invariably confusing. Their language also seems alien since most of these policies are designed to hold up in the complex legal systems.
One of the most important aspects of modern life is our privacy. One of the biggest problems in terms of privacy is the problem of protecting the privacy online. Any attempt to protect one’s privacy online begins with policies. These policies are extremely complex and invariably confusing. Their language also seems alien since most of these policies are designed to hold up in the complex legal systems.
 Modern technology has made it extremely difficult to do basic activities such as walking on the roads or driving a car without texting or fidgeting with mobile phones and androids. However, the Android allows users to text or email and walk or drive without even bothering to look at the screens. How? Simply ask and we will let you know.
Modern technology has made it extremely difficult to do basic activities such as walking on the roads or driving a car without texting or fidgeting with mobile phones and androids. However, the Android allows users to text or email and walk or drive without even bothering to look at the screens. How? Simply ask and we will let you know. The task of protecting the data was never an easy one. However, with the advent of internet viruses and hackers who are regularly developing new techniques to exploit or steal an individual’s data, the task has become a lot more difficult. There are cases where such attacks may not be as harmful to individual users. However, they can be a nightmare for financial institutions and the popular websites. The most common method to initiate a MITM attack is by uploading malware onto the user’s machine. However, the accuracy of this method is debatable as the method does not work sometimes.
The task of protecting the data was never an easy one. However, with the advent of internet viruses and hackers who are regularly developing new techniques to exploit or steal an individual’s data, the task has become a lot more difficult. There are cases where such attacks may not be as harmful to individual users. However, they can be a nightmare for financial institutions and the popular websites. The most common method to initiate a MITM attack is by uploading malware onto the user’s machine. However, the accuracy of this method is debatable as the method does not work sometimes.