 You should already know that a proxy server and firewall combination will prevent unauthorized access to your computer network from the outside, will anonymize the internet surfing you do and will ensure that no one will get into the network to infiltrate or damage your system. But what about those businesses that need either employees to access the network for remote work access? Or your online catalog that a customer can access to purchase items from you? Or what about the transfer of information in an upload or download section of your network? Obviously you don’t want to lock people out of your network that you want in your network to work or purchase from you.
You should already know that a proxy server and firewall combination will prevent unauthorized access to your computer network from the outside, will anonymize the internet surfing you do and will ensure that no one will get into the network to infiltrate or damage your system. But what about those businesses that need either employees to access the network for remote work access? Or your online catalog that a customer can access to purchase items from you? Or what about the transfer of information in an upload or download section of your network? Obviously you don’t want to lock people out of your network that you want in your network to work or purchase from you.
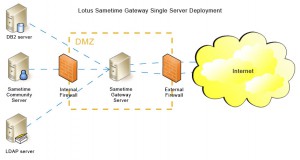
You should also already know that a proxy server will keep your internet surfing anonymous, and make internet access faster in addition to keeping your network safe. You buy anonymous proxy services to accomplish all this but there are some needs for some people to access at least a small part of your network. In this case, you need to create a DMZ (Demilitarized Zone). In war speak, a demilitarized zone is a geographic area where no fighting is occurring and no conflict is expected. In computer speak, it is an area of your network that is just on the other side of the firewall.
One analogy is that of the front yard of your house. You own that area, and you may even place lawn furniture or objects there, but you certainly wouldn’t leave anything of value in your front yard. For information that customers or employees must access for your business to operate smoothly, they need to continue to have access to that information.
Creating a DMZ is a simple procedure of placing one of your computers between the internet connection and the firewall protecting the rest of the network. This computer than becomes your DMZ which is programmable through most firewall software. Customers and employees are able to access this ‘DMZ’ but are not able to penetrate the network’s firewall to get at the more valuable information and sensitive data.
You can follow any responses to this entry through the RSS 2.0 feed.

Leave your comment